SOC 2® Trust Service Criteria: The 5 Pillars of Data Protection
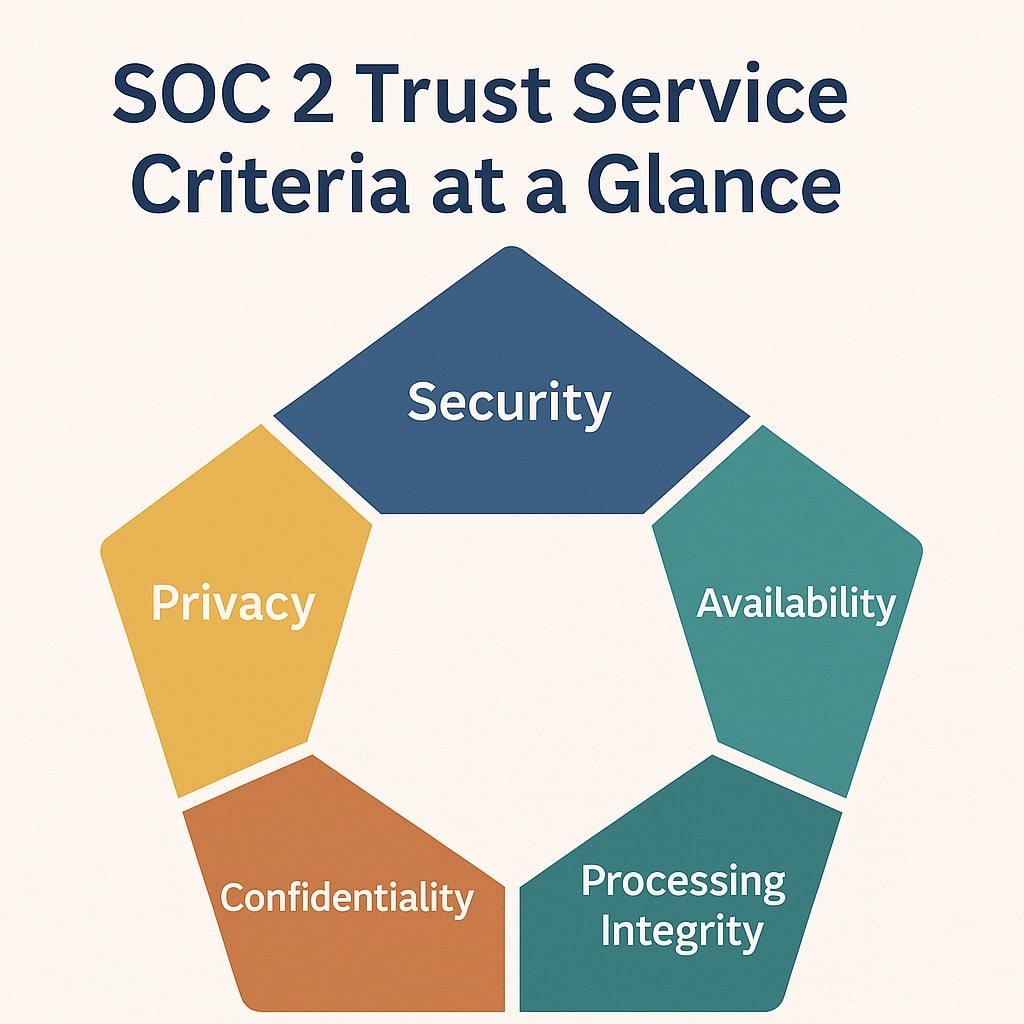
If your customers have started asking about SOC 2®, you’ve likely come across a somewhat abstract-sounding phrase: Trust Service Criteria. These five principles are at the heart of SOC 2®, and if you’re a startup or growing company aiming for compliance, you’ll need to understand what they mean, how they apply, and when to include […]
What is SOC 2® Compliance? Guide for founders.

Why you’re probably Googling this? You just got off a sales call, and your prospective customer asked the dreaded question: “Are you SOC 2® compliant?” If you’re the CEO or CTO of a growing SaaS business, this probably isn’t the first time. As customer expectations and security concerns rise, SOC 2 compliance is becoming a […]
