Beskar
Rails Security Engine
Multi-layered, proactive security for Rails applications. Named after Mandalorian armor because your app deserves legendary protection.
Why Beskar?
You already have Devise for authentication and Rack::Attack for rate limiting. But there's a gap between basic security hygiene and actually sleeping at night.
Without Beskar
- • Bots scanning /wp-admin on your Rails app (constantly)
- • Brute force attacks you don't even know about
- • Compromised accounts accessed from impossible locations
- • Manual IP blocking when you finally notice
- • No pattern detection or risk scoring
With Beskar
- ✓ WAF automatically detects and blocks vulnerability scans
- ✓ Smart rate limiting with pattern recognition
- ✓ Impossible travel detection locks suspicious accounts
- ✓ Automatic IP banning with escalating durations
- ✓ Comprehensive security event tracking and analysis
Beskar is the layer between basic authentication and paranoid security.
It learns from behavior, responds automatically, and gives you visibility into what's actually happening.
Security Features
Multiple layers of protection working together to secure your Rails application
Web Application Firewall
Detects and blocks vulnerability scanning across 12 attack categories including Rails exceptions, WordPress, PHP panels, path traversal, and framework debug endpoints.
Impossible Travel Detection
Automatically locks accounts when logins occur from physically impossible locations within a short timeframe using Haversine calculations.
Smart Rate Limiting
Distributed rate limiting using Rails.cache with IP and account-based throttling. Distinguishes single-account brute force from credential stuffing attacks.
Risk-Based Locking
Calculates authentication risk (0-100) based on geographic anomalies, device fingerprints, and IP reputation. Adaptive learning reduces scores for established patterns.
Persistent IP Banning
Hybrid cache + database blocking survives restarts. Escalating bans: 1h → 6h → 24h → 7d → permanent for repeat offenders.
IP Whitelisting
Trusted IPs (office networks, VPN gateways) bypass blocking while maintaining audit logs. CIDR notation and IPv6 supported.
Built-in Security Dashboard
Monitor security events, manage banned IPs, and analyze threats - all from a beautiful, mountable Rails engine dashboard
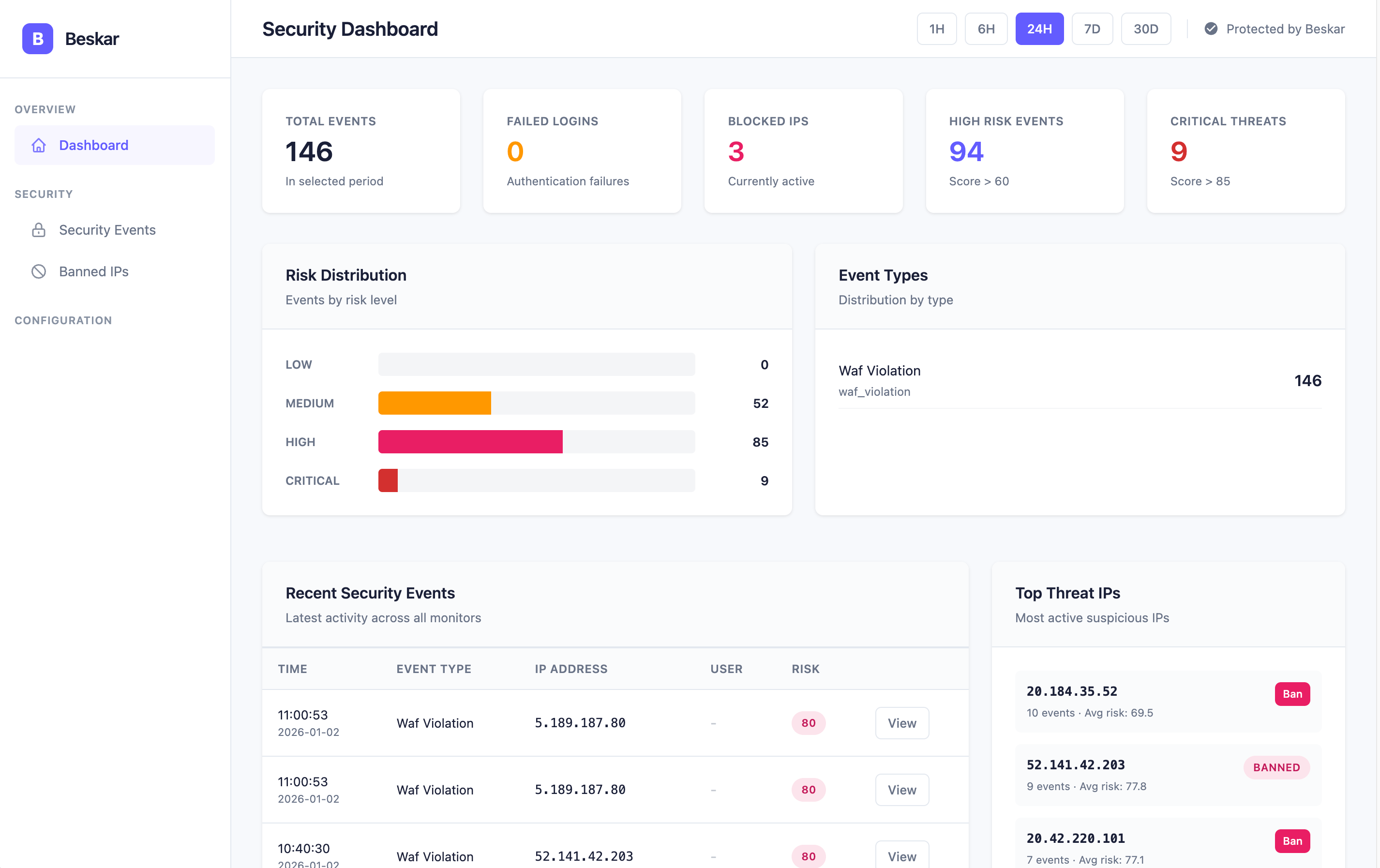
Security Overview Dashboard
Real-time metrics, event tracking, and threat visualization
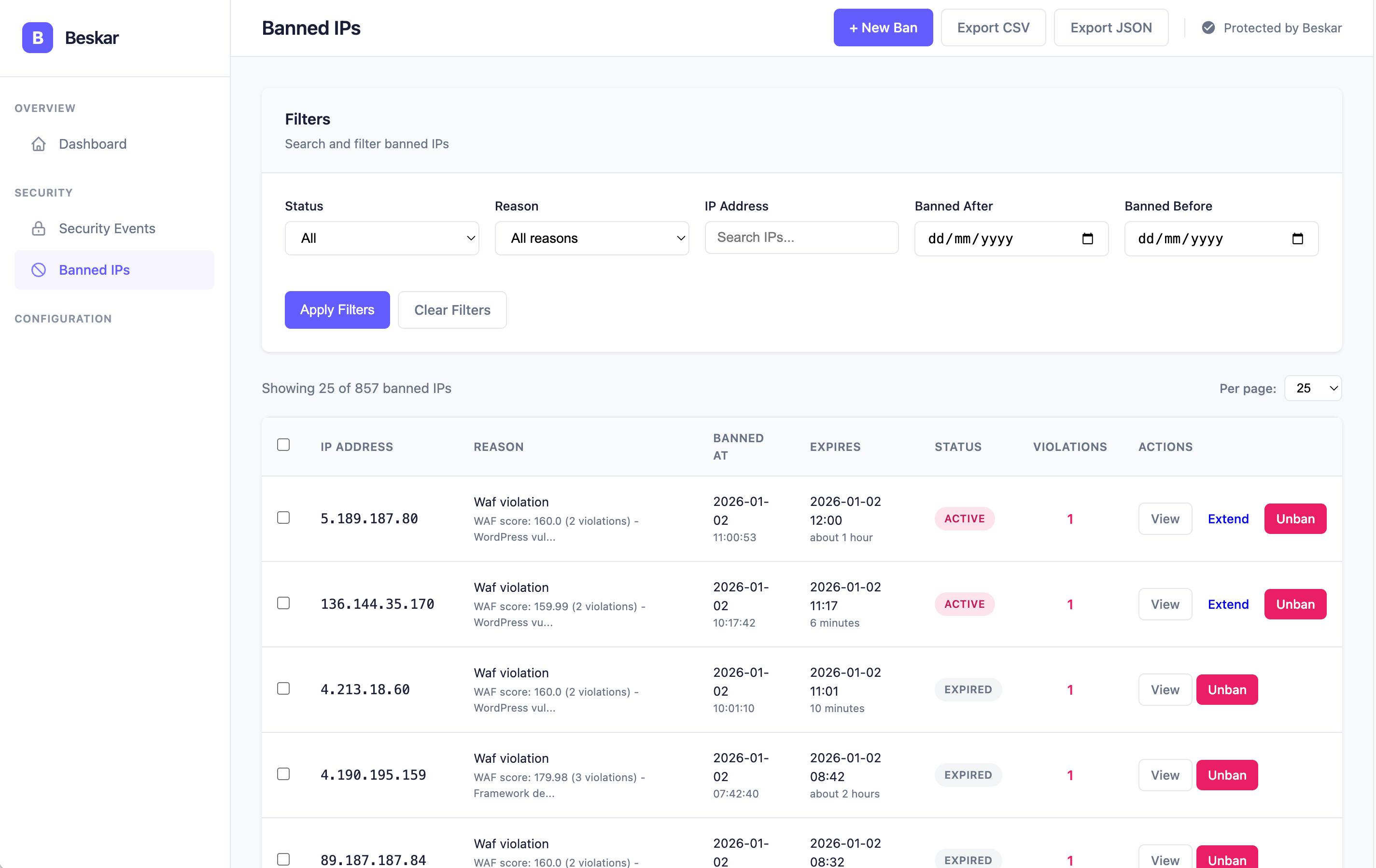
Banned IPs Management
View, manage, and whitelist IP addresses
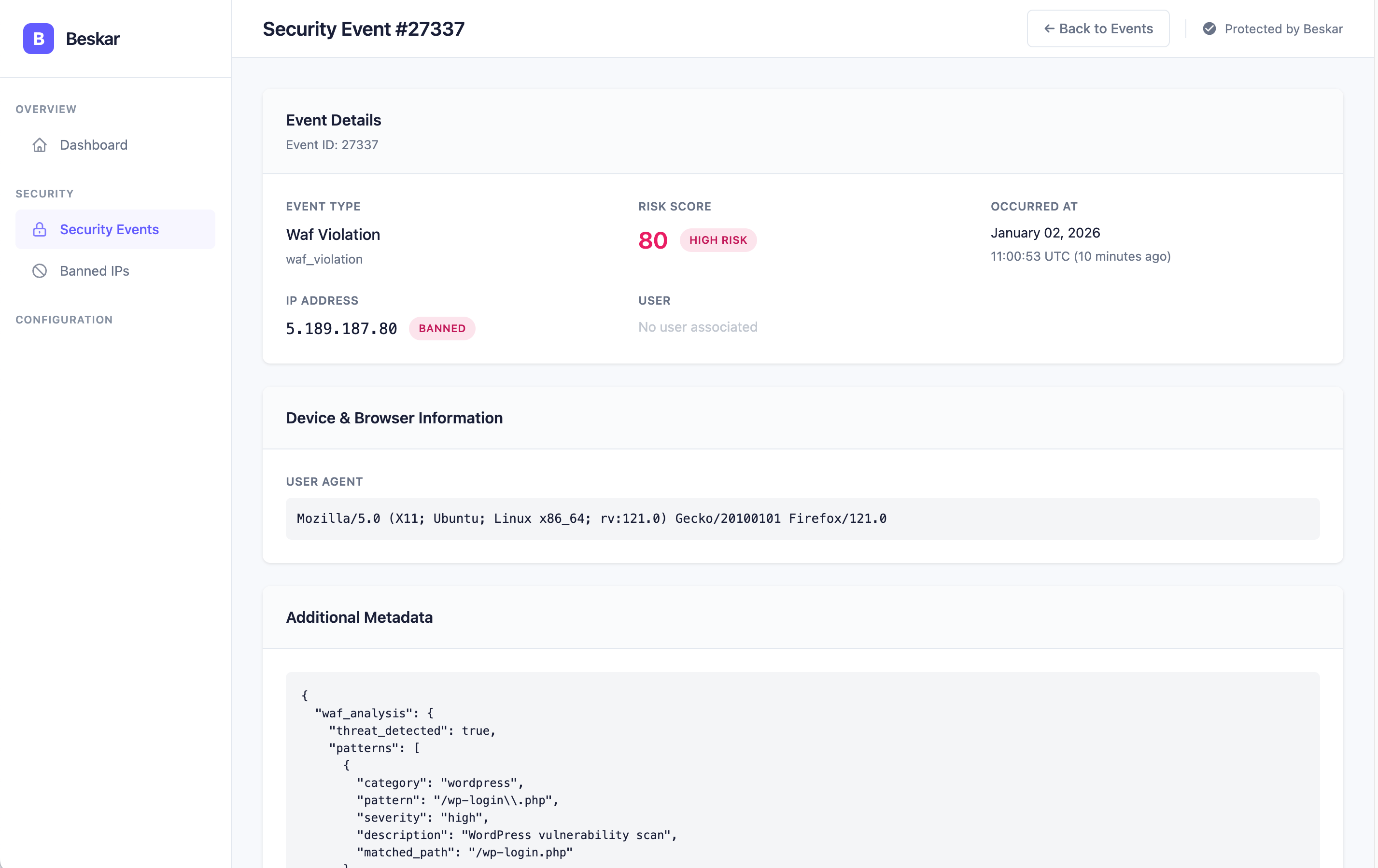
Security Event Details
Detailed event analysis with metadata
Custom Authentication
Configure dashboard access with your own authentication - Devise, token-based, or HTTP Basic Auth
Export Capabilities
Export security events for external analysis, compliance reporting, or SIEM integration
Geolocation Data
Visualize attack origins with MaxMind GeoLite2 integration for enhanced threat intelligence
Get Started in 5 Minutes
Add Beskar to your Rails application with just a few commands
Add to Gemfile
# Gemfile
gem 'beskar'
Install and Migrate
bundle install
bin/rails beskar:install
bin/rails db:migrate
Add to User Model
# app/models/user.rb
class User < ApplicationRecord
include Beskar::Models::SecurityTrackable
devise :database_authenticatable, :registerable, ...
end
Configure Dashboard Auth (Required)
Dashboard access requires explicit authentication. Configure in your initializer:
# config/initializers/beskar.rb
Beskar.configure do |config|
config.authenticate_admin = ->(request) do
user = request.env['warden']&.authenticate(scope: :user)
user&.admin?
end
end
Enable Blocking (Optional)
Beskar runs in monitor-only mode by default. Review events for 24-48 hours, then enable blocking:
# config/initializers/beskar.rb
Beskar.configure do |config|
config.waf = {
enabled: true,
monitor_only: false # Enable blocking
}
end
That's it! Beskar is now protecting your application.
View Full DocumentationFree & Open Source
Beskar is our contribution to the Rails community. Built by Humadroid as part of our commitment to open source security.
Built with ❤️ by the team at Humadroid
Using Beskar in production? We'd love to hear about it. Share your story on GitHub or reach out to us.
